Troubleshooting
Applies to: IBM StreamSets as a Service
Use the following tips for help with troubleshooting SAML authentication issues:
- SAML authentication is enabled for the organization, but no users can log in with SAML, including the organization administrator.
- If the IdP or the SAML configuration in Control Hub is incorrectly configured, no users can log in to IBM StreamSets with SAML authentication. In this case, a user with the Organization Administrator role can log in using local or public identity provider authentication to access the Control Hub organization SAML configuration page only.
- Some users are able to log in with SAML authentication, but other users cannot.
- For users that cannot successfully log in, verify that both of the following
statements are true:
- The user account exists in the IdP.
For example, if using Okta as your IdP, all users that need to log in to IBM StreamSets must be assigned to the IBM StreamSets app integration in Okta. If using Microsoft AD FS as your IdP, all users that need to log in to IBM StreamSets must exist in Microsoft Active Directory Domain Services (AD DS).
- The user account is invited to the Control Hub organization using the email address from the IdP.
If existing users joined the organization with a different email address before SAML authentication was enabled, you must add them to the Control Hub organization again using their email address from the IdP.
- The user account exists in the IdP.
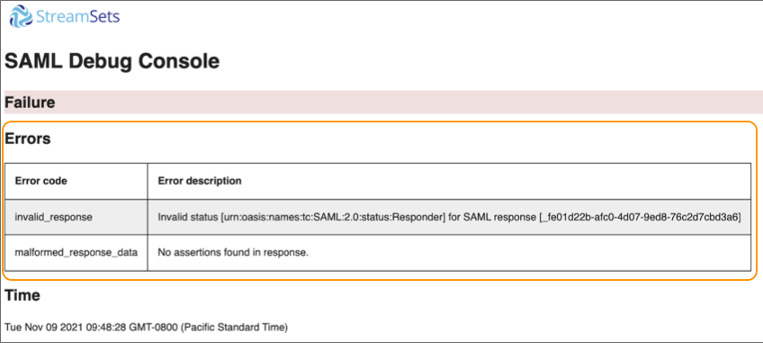
- When I test my SAML draft configuration, the SAML Debug Console indicates that the test has failed. How do I resolve this?
- When a test of a draft SAML configuration fails, the SAML Debug Console displays SAML error messages. Use these error messages to help you resolve the issue. Resolving the errors might require modifying your IdP configuration, modifying your SAML configuration in Control Hub, or modifying both configurations.