Enabling SAML using PingFederate
Applies to: IBM StreamSets as a Service
Step 1. Retrieve IdP Information
In Control Hub, choose PingFederate as your identity provider and then retrieve the IdP information generated for your organization.
- As a user with the Organization Administrator role, log in to IBM StreamSets using local or public identity provider authentication.
- In the Control Hub Navigation panel, click .
- Click Configure SAML.
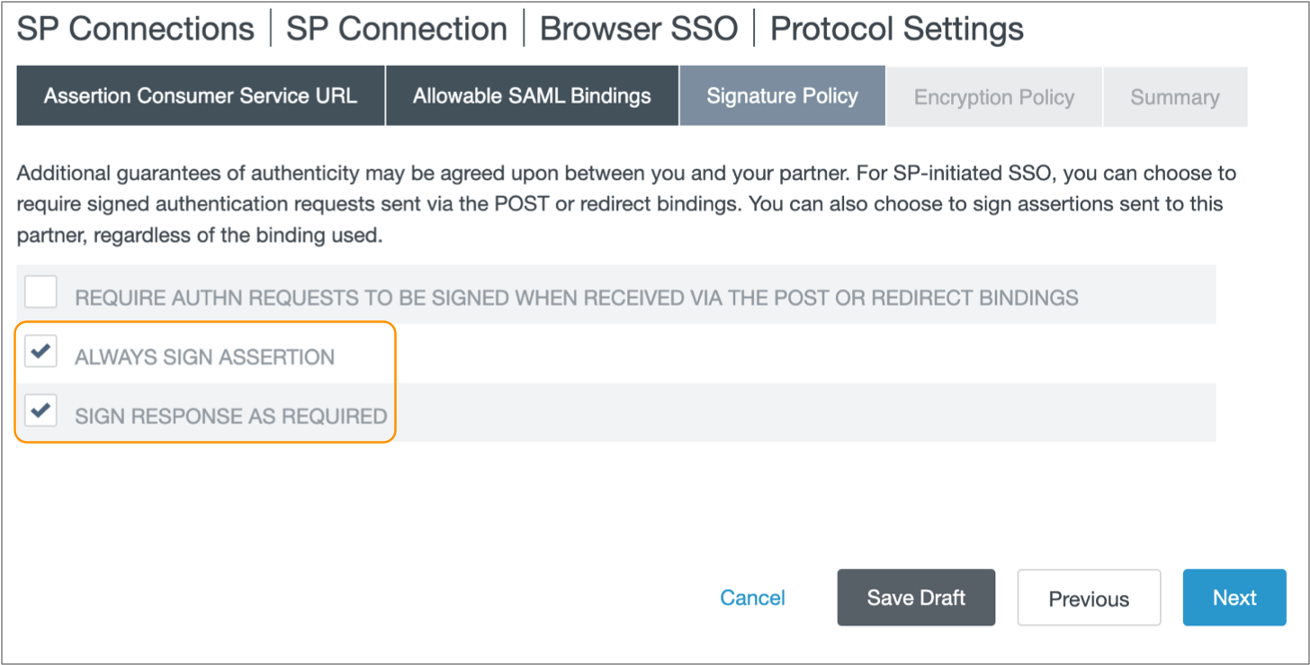
- Click the Draft tab.
-
Choose PingFederate as your SAML identity
provider.

-
In the IdP SAML Configuration section on the right, verify
that the Require Encryption on Assertion property is
enabled and then click Download StreamSets SAML
Metadata.
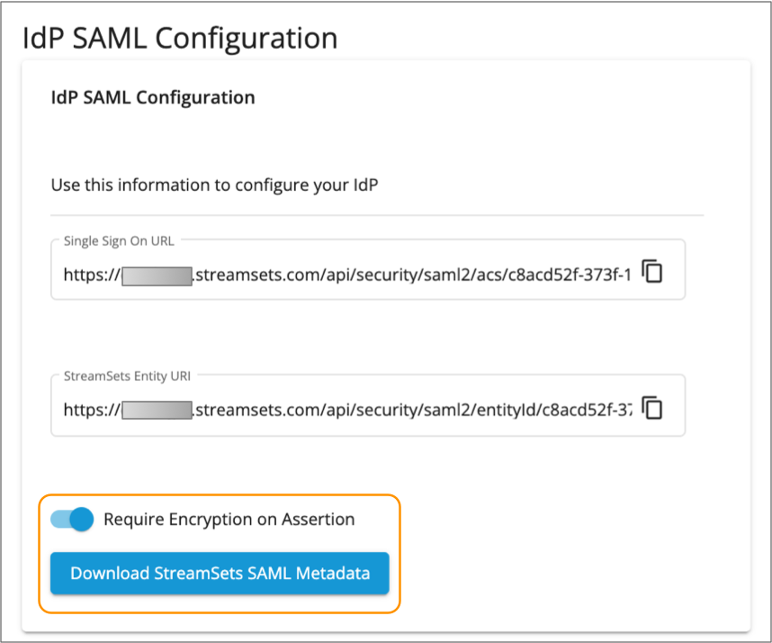
The metadata XML file is saved to your default downloads directory.
- Click Save to save the changes made to the draft SAML configuration.
Step 2. Create a PingFederate SP Connection
To register IBM StreamSets as a service provider in PingFederate, use the IdP information that you retrieved from Control Hub to create an SP connection in PingFederate.
When you create the SP connection, you specify the PingFederate IdP adapter and credential validator that retrieve and authenticate users against a data store such as LDAP. Any user added to the IdP adapter data store can log in to IBM StreamSets, as long as the user is invited to the Control Hub organization using the data store email address.
These steps provide brief instructions to create an SP connection in PingFederate. For detailed steps, see the PingFederate documentation.
- In the PingFederate administrative console, click .
- Click Create Connection.
- In the Connection Template tab, select Do not use a template for this connection, and then click Next.
-
In the Connection Type tab, select Browser SSO
Profiles and select SAML 2.0 for the
protocol.
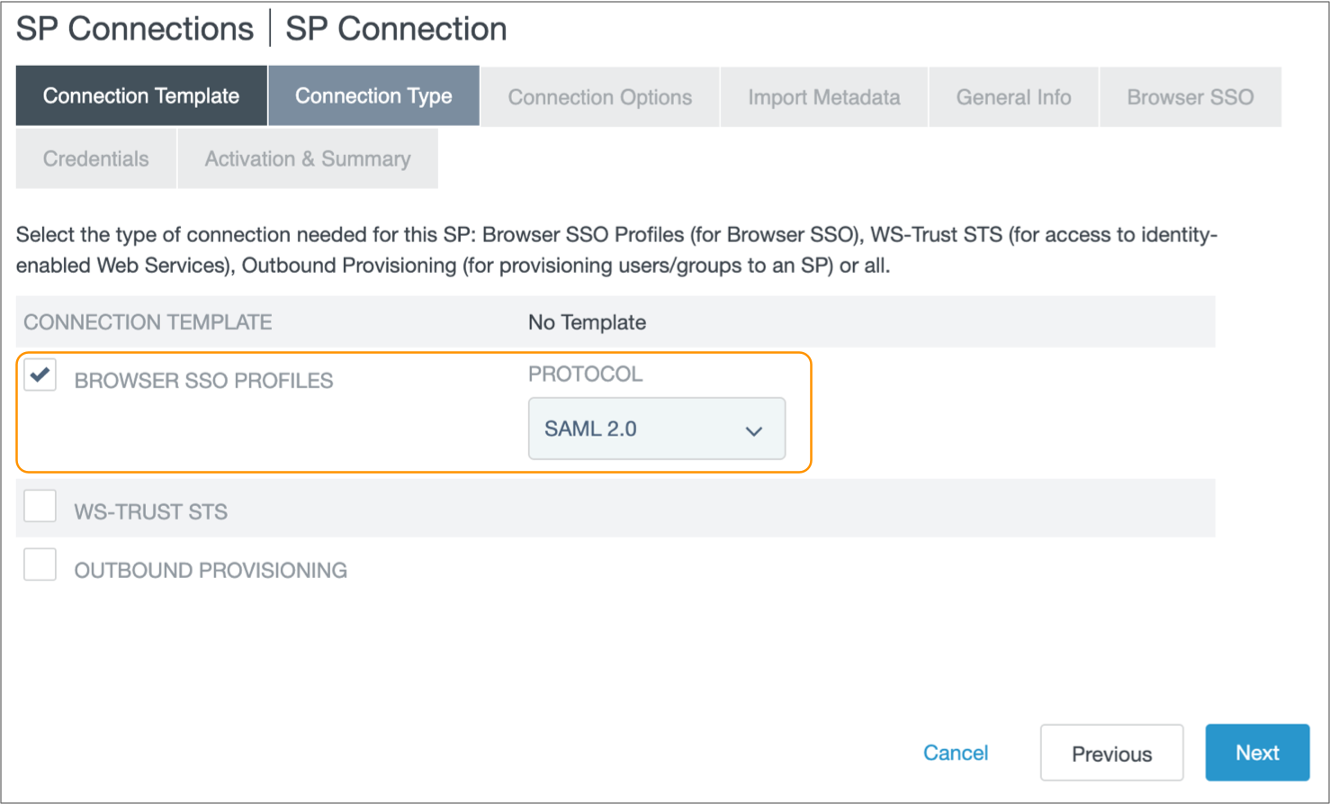
- Click Next.
- In the Connection Options tab, select Browser SSO and then click Next.
-
In the Import Metadata tab, select
File and then choose the metadata XML file that you
downloaded from Control Hub.
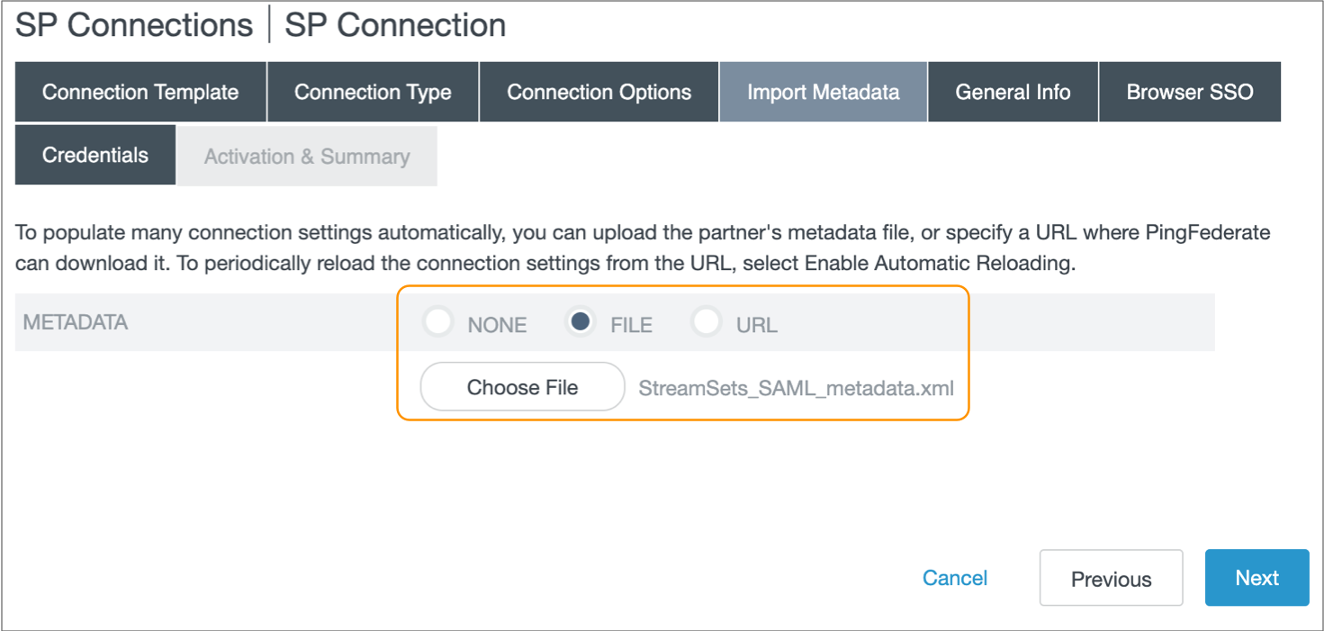
- Click Next.
- In the Metadata Summary tab, verify that the entity ID matches the StreamSets Entity URI displayed in the IdP SAML Configuration section in your Control Hub organization SAML settings, and then click Next.
-
In the General Info tab, enter general information for the
SP connection.
For example, you might enter StreamSets for the connection name and StreamSets Control Hub for the application name.
- Click Next.
- In the Browser SSO tab, click Configure Browser SSO.
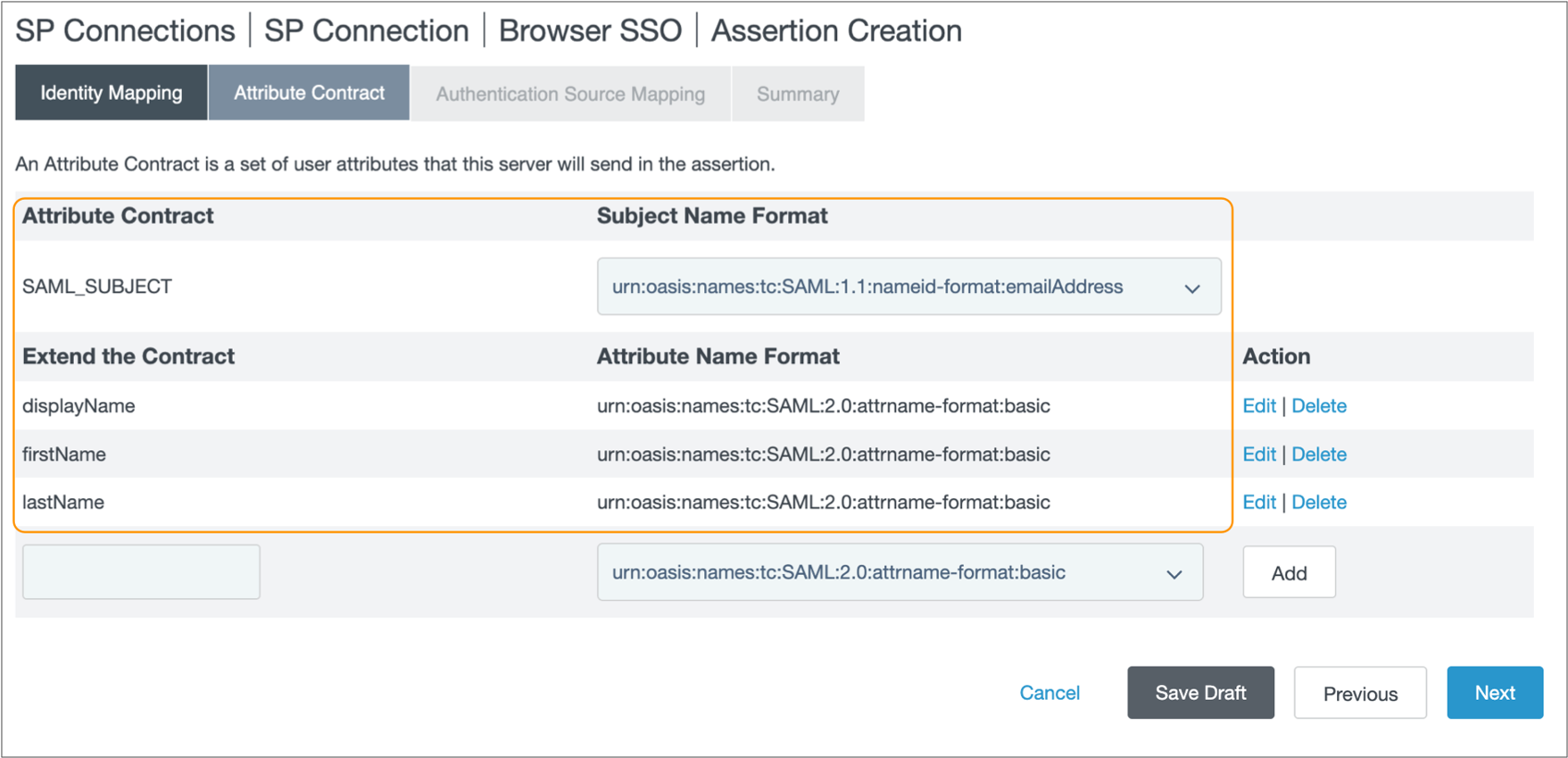
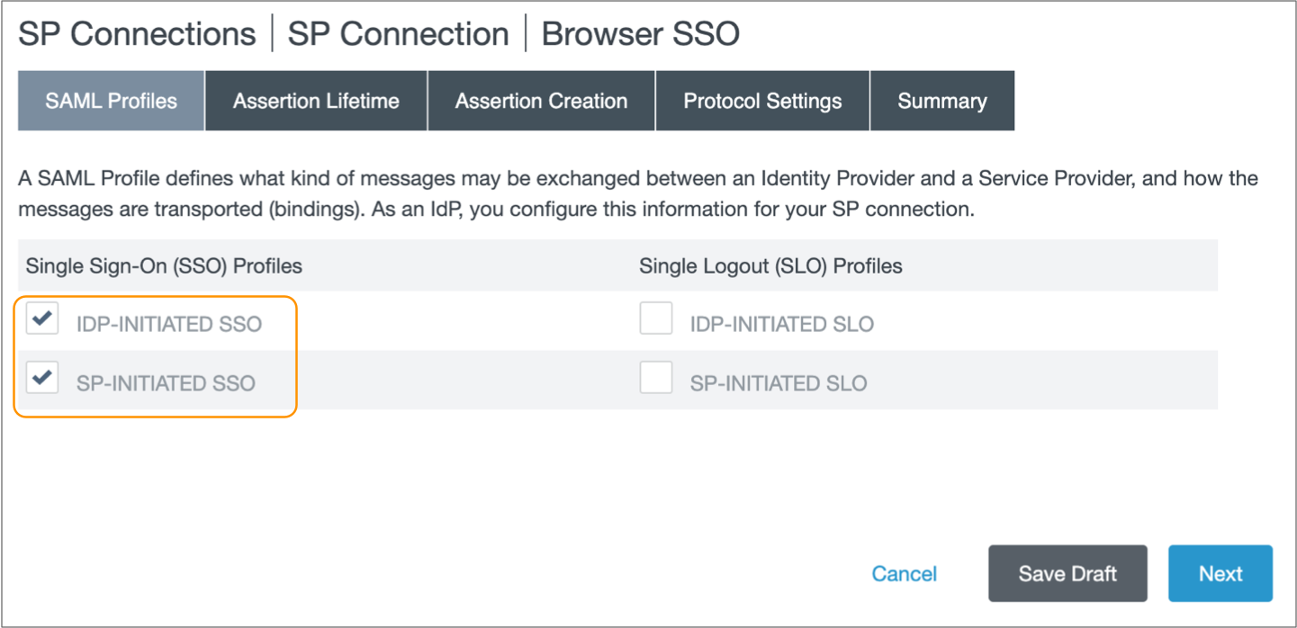
-
In the SAML Profiles tab in the Browser
SSO page, select IdP-initiated SSO and
SP-initiated SSO to enable both IdP and SP-initiated
logins.
If you plan to disable SP-initiated logins in your Control Hub organization settings, clear SP-initiated SSO. For more information, see IdP and SP-initiated Logins.
- Click Next.
- In the Assertion Lifetime tab, specify the assertion time frame and then click Next.
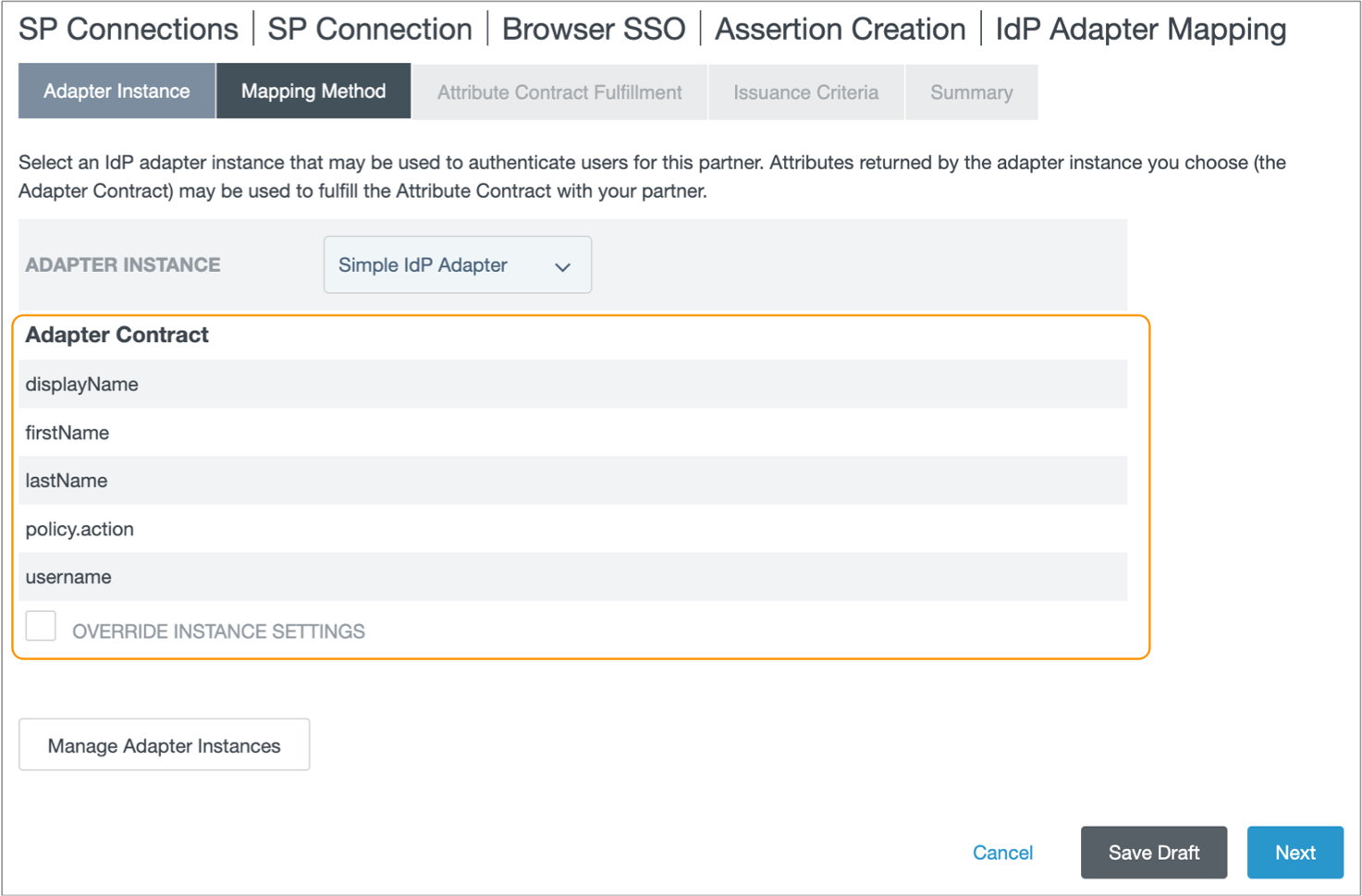
-
In the Assertion Creation tab, click Configure
Assertion Creation.
- In the Assertion Creation tab, click Next.
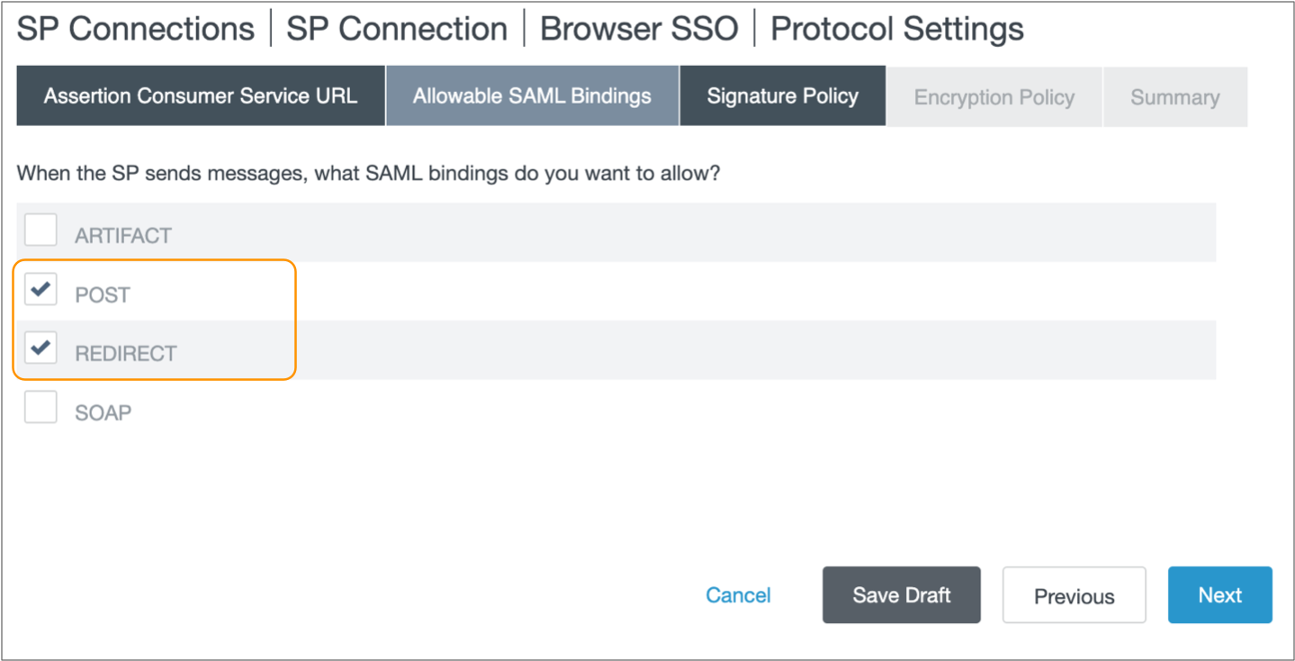
-
In the Protocol Settings tab, click Configure
Protocol Settings to configure the SP connection to encrypt the
SAML assertion.
- In the Protocol Settings tab, click Next.
- In the Browser SSO Summary tab, verify your configurations and then click Done.
- In the Browser SSO tab, click Next.
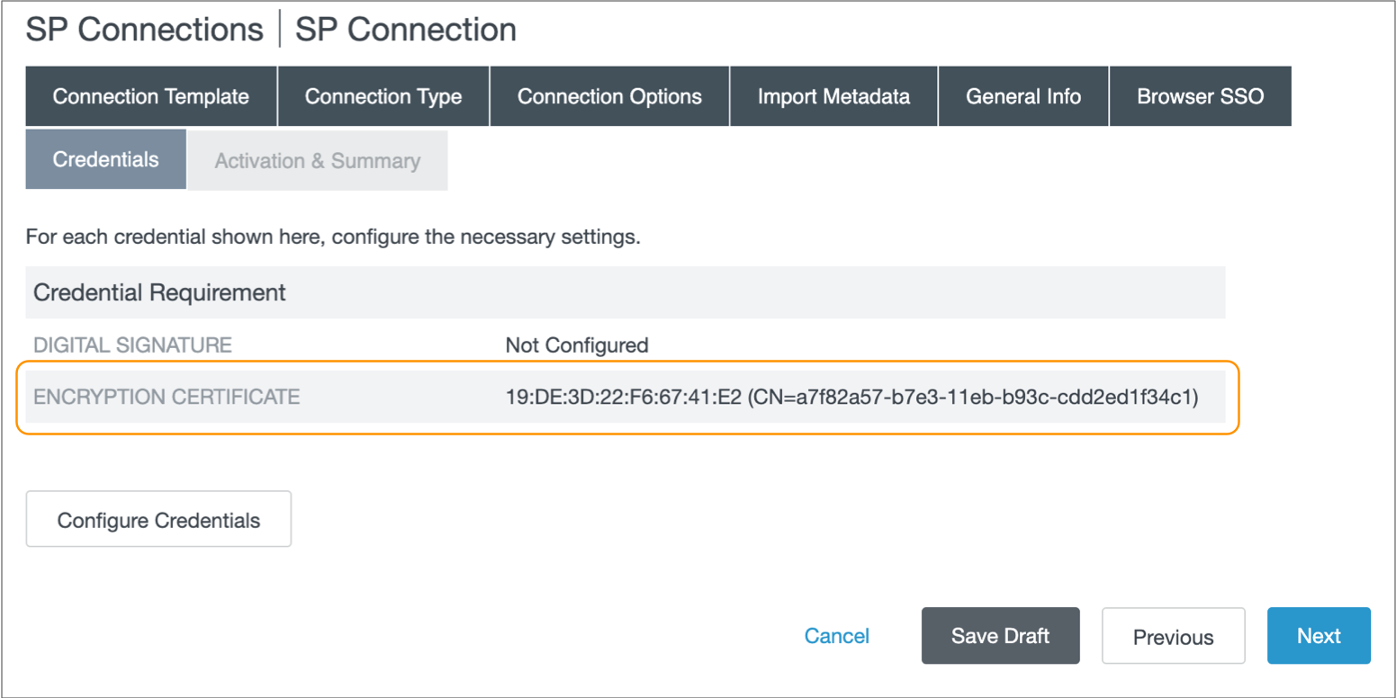
-
In the Credentials tab, verify that the encryption
certificate matches the certificate displayed in the List of SAML
Certificates section in your Control Hub organization SAML settings.
Note: The encryption certificate is automatically imported with the IBM StreamSets metadata XML file. However, if you incorrectly follow the previous steps and do not enable assertion encryption, then PingFederate removes the encryption certificate.
-
Click Configure Credentials.
Select the signing certificate that you use for PingFederate SP connections, and then click Next and then Done to return to the Credentials tab.
- Click Next.
- In the Activation & Summary tab, verify your configurations and then click Save.
- In the SP Connections page, locate the SP connection that you just created, and then click to download the PingFederate Metadata XML.
Step 3. Set up a Draft SAML Configuration
In Control Hub, set up the draft SAML configuration for your organization by uploading the metadata XML file downloaded from PingFederate, and then optionally configuring advanced properties. You can also enable or disable SP-initiated logins.
- In the Control Hub Navigation panel, click .
- Click Configure SAML.
- Click the Draft tab.
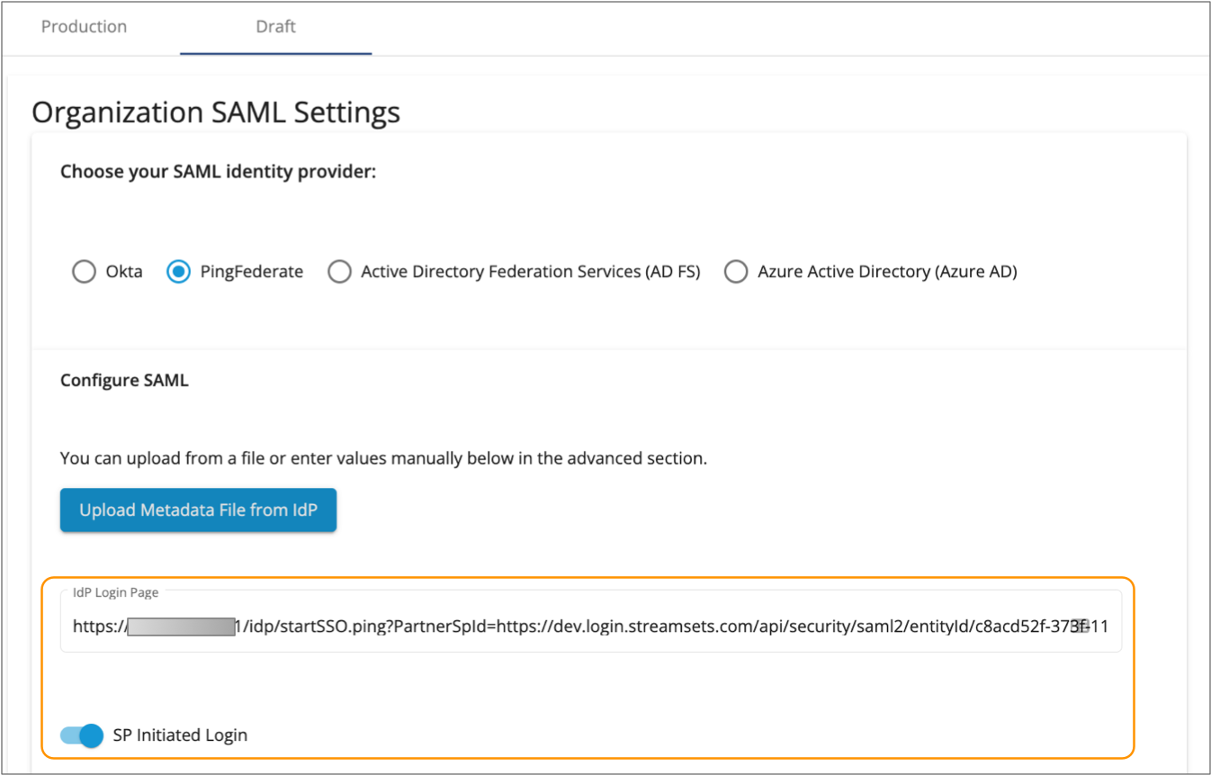
-
In the Organization SAML Settings section, click
Upload Metadata File from IdP and upload the metadata
file that you downloaded from PingFederate.
By default, the IdP Login Page property is automatically populated from the uploaded metadata, and SP-initiated logins from IBM StreamSets are enabled, as follows:
-
To disable SP-initiated logins and require IdP-initiated logins, disable the
SP Initiated Login property.
For more information, see IdP and SP-initiated Logins.
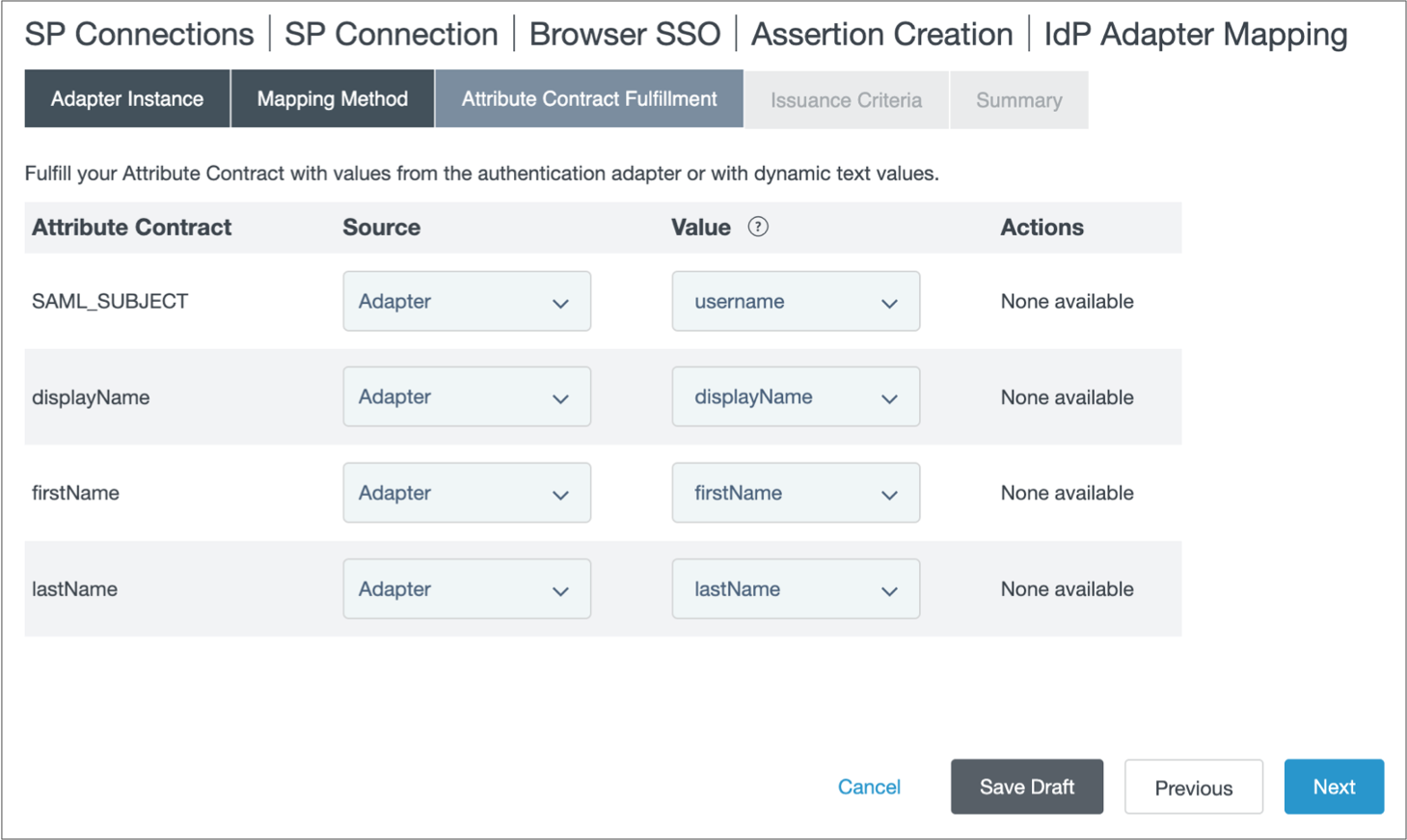
-
If you created attribute mappings in PingFederate that do not match the default
values displayed for the IdP user properties, modify the property values as
needed.
If you created the attribute mappings as instructed in Step 2. Create a PingFederate SP Connection, you can use the default values. For more information, see IdP Attribute Mappings.
-
Optionally, click Show Advanced and modify the advanced
properties.
Control Hub automatically populates the advanced property values from the uploaded metadata file. In most cases, you do not need to modify the advanced properties.
- Click Save.
-
If you enabled SP-initiated logins, click Test to test
the configuration.
The SAML debug console displays, indicating whether IBM StreamSets is able to successfully send a request to PingFederate and receive a response. In case of a failure, use the listed errors to help you troubleshoot issues.
Step 4. Publish and Enable the SAML Configuration
After testing and validating that the draft SAML configuration is set up correctly with PingFederate, publish the configuration to production and then enable the configuration to activate it.
- In the Draft tab, click Publish in the Organization SAML Settings section.
-
Click Confirm.
The Production tab displays a read-only version of the SAML configuration.
- In the Production tab, click Enable to enable SAML authentication for your organization.
-
Click Confirm.
When enabled, all organization users must log in using SAML authentication. For more information, see IdP and SP-initiated Logins.
To invite new users to the organization, first verify that the users exist in the IdP adapter data store specified for the PingFederate SP connection. Then in Control Hub, use the email addresses from PingFederate to invite the users. For more information, see Adding Users.
If existing organization users are PingFederate users and originally joined with their email address from PingFederate, they can use SAML authentication for the next login session. If existing organization users joined with a different email address, you must add them to the Control Hub organization again using their email address from PingFederate.