Credential Stores
When your organization uses deployed Transformer for Snowflake engines, you can configure Transformer for Snowflake to access sensitive information that is secured in a credential store.
Transformer for Snowflake pipelines that run on deployed engines use connections to connect to Snowflake. When you configure a connection, you specify sensitive information, such as user names and passwords or private keys.
When you enter sensitive information directly in connection properties, users with certain roles, such as Deployment Manager, can access that information from the engine installation directory.
To best secure sensitive information, add the data as secrets to a credential store and then use credential functions in credential properties to retrieve those values.
Defining secrets in a credential store can also make it easier to migrate pipelines to another environment. For example, if you migrate multiple pipelines from a development to a production environment, you do not need to edit each pipeline with details for the production environment. You can simply replace the development credential store with the production version.
You can configure Transformer for Snowflake to use multiple credential stores. Each credential store is identified by a unique credential store ID.
Enabling Credential Stores
You can configure Transformer for Snowflake to use one or more credential stores. Each credential store is identified by a unique credential store ID.
- credentialStores property
- This property defines the credential stores that Transformer for Snowflake can use.
- Sets of related properties
- Each supported credential store type has a set of related properties. The
property names include the default credential store IDs originally specified
in the
credentialStoresproperty.
For example, say you want to use two AWS credential stores, awsDev for
development and awsProd for production. To do this, you specify the
credential store IDs in the credentialStores property and make a copy
of the related AWS credential store properties, so you have one set for each credential
store.
awsDev, and you do the
same for awsProd. The resulting properties might look as follows, with
important changes in bold:
##############################################################
# Transformer for Snowflake Credential Stores #
##############################################################
credentialStores=awsDev,awsProd
#credentialStores.usePortableGroups=false
################################################################
# awsDev: AWS Secrets Manager Credential Store Configuration #
################################################################
# The following properties are for an AWS Secrets Manager credential store that uses the 'aws'
# default credential store ID. If you specified a custom ID in the credentialStores property,
# replace 'aws' in the property names with the custom ID.
# Defines the implementation of the 'aws' credential store
# Update 'aws' in the property name as needed, but do not change the definition of this property.
credentialStore.awsDev.def=streamsets-transformer-aws-secrets-manager-credentialstore-lib::com_streamsets_datacollector_credential_aws_secrets_manager_AWSSecretsManagerCredentialStore
# Default name-key separator for the name parameter in credential functions
credentialStore.awsDev.config.nameKey.separator=&
# AWS region
credentialStore.awsDev.config.region=us-west-1
# AWS access key
credentialStore.awsDev.config.access.key=AWSACCESSKEYDEV
# AWS secret key
credentialStore.awsDev.config.secret.key=AWS/CONFIG/SECRETKEYDEV
# Secrets max cache size
# Maximum number of secrets to cache locally
credentialStore.awsDev.config.cache.max.size=1024
# Secrets cache TTL
# The number of milliseconds that a cached secret is considered valid before requiring a refresh
# The default is equivalent to 1 hour
credentialStore.awsDev.config.cache.ttl.millis=3600000
# Requires a group secret for each secret
credentialStore.awsDev.config.enforceEntryGroup=false
################################################################
# awsProd: AWS Secrets Manager Credential Store Configuration #
################################################################
# The following properties are for an AWS Secrets Manager credential store that uses the 'aws'
# default credential store ID. If you specified a custom ID in the credentialStores property,
# replace 'aws' in the property names with the custom ID.
# Defines the implementation of the 'aws' credential store
# Update 'aws' in the property name as needed, but do not change the definition of this property.
credentialStore.awsProd.def=streamsets-transformer-aws-secrets-manager-credentialstore-lib::com_streamsets_datacollector_credential_aws_secrets_manager_AWSSecretsManagerCredentialStore
# Default name-key separator for the name parameter in credential functions
credentialStore.awsProd.config.nameKey.separator=&
# AWS region
credentialStore.awsProd.config.region=us-west-1
# AWS access key
credentialStore.awsProd.config.access.key=AWSACCESSKEY
# AWS secret key
credentialStore.awsProd.config.secret.key=AWS/CONFIG/SECRETKEY
# Secrets max cache size
# Maximum number of secrets to cache locally
credentialStore.awsProd.config.cache.max.size=1024
# Secrets cache TTL
# The number of milliseconds that a cached secret is considered valid before requiring a refresh
# The default is equivalent to 1 hour
credentialStore.awsProd.config.cache.ttl.millis=3600000
# Requires a group secret for each secret
credentialStore.awsProd.config.enforceEntryGroup=falseGroup Access to Secrets
As an additional layer of security, you can employ user groups to further limit access to the secrets defined in credential stores.
- Required group argument in credential functions
- Credential functions include a group argument that defines the user group that can access the secret. The group argument ensures that the user who attempts to preview, validate, or start a pipeline that includes a credential function belongs to the group specified in the function. The user must also have execute permission on the pipeline.
- Optional group secrets in the credential store
-
In addition to using the group argument in credential functions, you can configure Transformer for Snowflake to require group secrets for a credential store.
To require the use of group secrets, in the Transformer for Snowflake credential store configuration properties, set the
credentialStore.<cstore ID>.config.enforceEntryGroupproperty totrue.A group secret is a secret defined in the credential store that contains a comma-delimited list of Transformer for Snowflake user groups permitted to access the associated secret.
When the credential store ID requires group secrets, you must define a group secret for every secret that Transformer for Snowflake accesses in that credential store. The name of the group secret is based on the secret name, as follows:
When you configure a credential function to call a secret, the user group specified in the credential function must be listed in the associated group secret that is defined in the credential store.<secret name>-groups
${credential:get("aws", "awsprod@9a213-b18-1eb-b9c-15ad68", accesskeyprod)}- The user who starts the pipeline is in the
awsproduser group. - The
accesskeyprodsecret has an associatedaccesskeyprod-groupsgroup secret defined in the credential store. - The
accesskeyprod-groupsgroup secret includes theawsproduser group.
When Transformer for Snowflake is not configured to require group secrets, Transformer for Snowflake validates only the first point, verifying that the user belongs to the specified group.
Sensitive Data in Credential Store Properties
When you define credential store properties, you must enter some sensitive data such as passwords to authenticate with the credential store system. For example, to use the AWS Secrets Manager credential store system, you enter the AWS access key ID and secret access key.
To prevent exposing the sensitive data in the Control Hub deployment details, Control Hub displays the sensitive values as REDACTED after you save the deployment.
Alternatively, instead of entering sensitive data in the configuration properties, you can protect the sensitive data by storing the data in an external location and then using functions to retrieve the data. When you use functions in credential store properties, Control Hub does not redact the credential store property values. Control Hub displays the defined functions after you save the deployment.
AWS Secrets Manager
To use the AWS Secrets Manager credential store system, define the configuration properties used to connect to Secrets Manager. Then, call credential functions in pipeline or stage properties to retrieve stored values.
In Secrets Manager, you must configure an access and secret key pair with correct permission to read the key. To follow best practices, make secrets read-only and limit access. See the Secrets Manager documentation on identity and access management (IAM) policies.
Configure AWS Secrets Manager Properties
To enable Transformer for Snowflake to connect to the AWS Secrets Manager credential store, configure the Secrets Manager properties in the Transformer for Snowflake credential store configuration properties.
- In Control Hub, edit the deployment, and in the Configure Engine section, click Advanced Configuration. Then, click Credential Stores.
- Uncomment the credentialStores property in the file and
specify the credential store ID to use. Use only alphabetic characters for the
credential store ID.
By default, the property lists a default credential store ID for each type of credential store, such as
azurefor Azure Key Vault. When using only one credential store of any type, it's simplest to use the default value.To use a single Secret Manager, set the value to
aws. To enable multiple credential stores, specify a comma-separated list of credential store IDs. For example, to use multiple Secret Manager credential stores, simply specify separate IDs for each, such asawsDev,awsProd. - Uncomment and configure the following properties as needed.
If you specified a custom credential store ID, update the names of the following properties, replacing
awswith the custom ID. When using the default credential store ID, leave the property names as they are.To use multiple AWS Secrets Manager credential stores, make a copy of the properties for each credential store. Then, update the credential store ID in each set of property names before defining the properties. For an example, see Enabling Credential Stores.Note: Control Hub displays sensitive data such as passwords asREDACTEDafter you save the deployment.These properties are grouped in the AWS Secrets Manager section of the file:
Secrets Manager Property Description credentialStore.<cstore ID>.def Required. Defines the implementation of the AWS Secrets Manager credential store. Do not change the default value.
credentialStore.<cstore ID>.config.nameKey.separator Optional. Separator to use in the nameargument for credential functions.Note: In Secrets Manager, names can contain alphanumeric and the following special characters:/ _ + = . @ -. Therefore, avoid using those characters as separators.credentialStore.<cstore ID>.config.region Required. AWS region that hosts Secrets Manager. For a list of available regions, see the AWS Region Table. credentialStore.<cstore ID>.config.access.key Required when using access keys to authenticate with AWS. AWS access key. credentialStore.<cstore ID>.config.secret.key Required when using access keys to authenticate with AWS. AWS secret key. credentialStore.<cstore ID>.config.cache.max.size Optional. Maximum number of secrets Transformer for Snowflake can cache locally. Default is 1024.
credentialStore.<cstore ID>.config.cache.ttl.millis Optional. Number of milliseconds that Transformer for Snowflake considers a cached secret valid before requiring a refresh. Default is 1 hour.
credentialStore.<cstore ID>.config.enforceEntryGroup Optional. Requires Transformer for Snowflake to verify if a user who previews, validates, or starts the pipeline belongs to the group that is permitted to access the secret. When set to true, each secret must have the corresponding
<secret name>-groupssecret that contains a comma-separated list of groups that is permitted to access the secret.For more information, see Group Access to Secrets.
Default is false.
- Save the changes to the deployment and restart all engine instances.
Azure Key Vault
Before Transformer for Snowflake can connect to the Microsoft Azure Key Vault credential store system, you must complete several prerequisites in Azure so that Transformer for Snowflake can access the Azure Key Vault as an application.
After completing the prerequisites, define the configuration properties used to connect to Azure Key Vault. Then, define credential functions in stage or pipeline properties to retrieve stored values.
Prerequisites
Before Transformer for Snowflake can connect to the Microsoft Azure Key Vault credential store system, you must complete the following prerequisites within Azure:
- Register Transformer for Snowflake with Azure Active Directory
- Use the Azure portal to register Transformer for Snowflake as an application in Azure Active Directory. When an application such as Transformer for Snowflake accesses secrets in an Azure key vault, the application must use an authentication token from Azure Active Directory.
- Authorize Transformer for Snowflake to use keys or secrets in the Azure key vault
- Use the Azure portal to authorize Transformer for Snowflake to use the keys or secrets in the Azure key vault. Azure Key Vault requires that applications be authorized to access each key vault.
Configure Azure Key Vault Properties
To enable Transformer for Snowflake to connect to the Azure Key Vault credential store, configure the Azure Key Vault properties in the Transformer for Snowflake credential store configuration properties.
- In Control Hub, edit the deployment, and in the Configure Engine section, click Advanced Configuration. Then, click Credential Stores.
- Uncomment the credentialStores property in the file and
specify the credential store ID to use. Use only alphabetic characters for the
credential store ID.
By default, the property lists a default credential store ID for each type of credential store, such as
awsfor AWS Secrets Manager. When using only one credential store of any type, it's simplest to use the default value.To use a single Azure Key Vault, set the value to
azure. To enable multiple credential stores, specify a comma-separated list of credential store IDs. For example, to use multiple Azure Key Vault credential stores, simply specify separate IDs for each, such asazureDev,azureProd. - Uncomment and configure the following properties as needed.
If you specified a custom credential store ID, update the names of the following properties, replacing
azurewith the custom ID. When using the default credential store ID, leave the property names as they are.To use multiple Azure Key Vault credential stores, make a copy of the properties for each credential store. Then, update the credential store ID in each set of property names before defining the properties. For an example, see Enabling Credential Stores.
The properties are grouped in the Azure Key Vault section of the file:Note: Control Hub displays sensitive data such as passwords asREDACTEDafter you save the deployment. -
Azure Key Vault Property Description credentialStore.<cstore ID>.def Required. Defines the implementation of the Azure Key Vault credential store. Do not change the default value.
credentialStore.<cstore ID>.config.credential.refresh.millis Optional. Number of milliseconds that Transformer for Snowflake locally caches a secret. When the time expires, Transformer for Snowflake retrieves the secret from Azure Key Vault. credentialStore.<cstore ID>.config.credential.retry.millis Optional. Number of milliseconds that Transformer for Snowflake waits before attempting to retry a retrieval of a secret from Azure Key Vault, in the case of an error. credentialStore.<cstore ID>.config.vault.url Required. URL to the key vault created in Azure Key Vault. Use the following format:
https://<key vault name>.vault.azure.net/credentialStore.<cstore ID>.config.client.id Required. Application ID assigned to Transformer for Snowflake when you registered Transformer for Snowflake as an application in Azure Active Directory, as described in Prerequisites. credentialStore.<cstore ID>.config.client.key Required. Authentication key assigned to Transformer for Snowflake when you registered Transformer for Snowflake as an application in Azure Active Directory, as described in Prerequisites. credentialStore.<cstore ID>.config.enforceEntryGroup Optional. Requires Transformer for Snowflake to verify if the user who previews, validates, or starts the pipeline belongs to a group that is permitted to access the secret. When set to true, each secret must have a corresponding
<secret name>-groupssecret that contains a comma-separated list of groups that is permitted to access the secret.For more information, see Group Access to Secrets.
Default is false.
- Save the changes to the deployment and restart all engine instances.
Calling Secrets from the Pipeline
Specify credential functions in connection properties to retrieve secrets stored in a credential store.
Use the credential functions in any property that displays the key icon next to it. For example, you can use credential functions in the User, Password, and Role properties below:
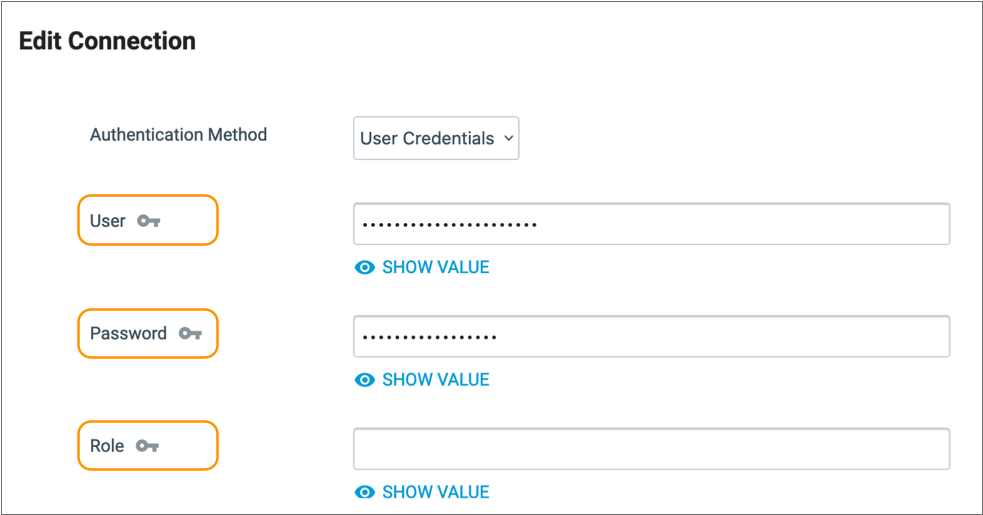
When you use a credential function in a connection property, the function must be the only value defined in the property. For details about credential functions, see Credential Functions.
Credential Functions
Credential functions provide access to sensitive information, such as user names and passwords, that is secured in a credential store. Use credential functions in connection properties to enable Transformer for Snowflake to access external systems without exposing those values.
Before you use a credential function, you must configure Transformer for Snowflake to use one of the supported credential stores.
You can use credential functions in any property that displays a key icon next to the property name. For example:

You can replace any argument with a literal or an expression that evaluates to the argument. String literals must be enclosed in single or double quotation marks.
- credential:get(<cstoreId>, <userGroup>, <name>)
- Returns the secret from the credential store. Uses the following
arguments:
- cstoreId - Unique ID of the credential store to use. Use the ID specified in the Transformer for Snowflake credential store configuration properties. For more information, see Enabling Credential Stores.
- userGroup - Group that a user must belong to in order to access the
secret. Only users that have execute permission on the pipeline and
that belong to this group can validate, preview, or run the pipeline
that retrieves the secret. Specify the group using the required naming convention:
<group ID>@<organization ID>.Note: The organization ID differs from the organization name. It is an alphanumeric string that you can find by going to Manage > My Organization.To grant access to all users, specify the default group using
allorall@<organization ID>. - name - Name of the secret to retrieve from the credential store. Use
the required format for the credential store:
- AWS Secrets Manager - Enter the name of the secret to
retrieve from Secrets Manager. Use the following format:
"<name><separator><key>", where:<name>is the name of the secret in Secrets Manager to read.<separator>is the separator defined in the Transformer for Snowflake credential store configuration properties.<key>is the key for the value that you want returned.
- Azure Key Vault - Enter the name of the key or secret to retrieve from Azure Key Vault.
- AWS Secrets Manager - Enter the name of the secret to
retrieve from Secrets Manager. Use the following format:
- credential:getWithOptions(<cstoreId>, <userGroup>, <name>, <storeOptions>)
- Returns the secret from the credential store using additional options to communicate with the credential store.